
Week 9. Editorial
TL;DR
This is an Ubuntu 22.04 machine owned by an editorial. It runs a web application where users can upload and publish their books, but the upload form is vulnerable to SSRF. Exploiting it we can disclose credentials for a low-priv SSH shell. Regarding escalation, we find credentials for a lateral movement inside the commit history of an internal Git repository. Then, we abuse sudo configuration and a vulnerable GitPython library (CVE-2022-24439) to get a root shell.
KEYWORDS
SSRF, Git enumeration, GitPython 3.1.29, CVE-2022-24439, sudo escalation.
REFERENCES
https://medium.com/stolabs/git-exposed-how-to-identify-and-exploit-62df3c165c37 https://www.cvedetails.com/cve/CVE-2022-24439/ https://security.snyk.io/vuln/SNYK-PYTHON-GITPYTHON-3113858
ENUMERATION
Port scan.
> nmap $target -p- --min-rate=5000 -Pn --open --reason
Starting Nmap 7.93 ( https://nmap.org ) at 2024-09-30 13:14 EDT
Nmap scan report for 10.10.11.20
Host is up, received user-set (0.054s latency).
Not shown: 57362 closed tcp ports (conn-refused), 8171 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack
Nmap done: 1 IP address (1 host up) scanned in 16.03 secondsEnumerate the open ports.
Add to hosts file and enumerate with Firefox. A editorial's website comes into view, where visitors can upload and publish their books.

Click on "Publish with us", a form to upload files comes into view. Notice there is a box to upload covers from a URL, this looks candidate for SSRF.
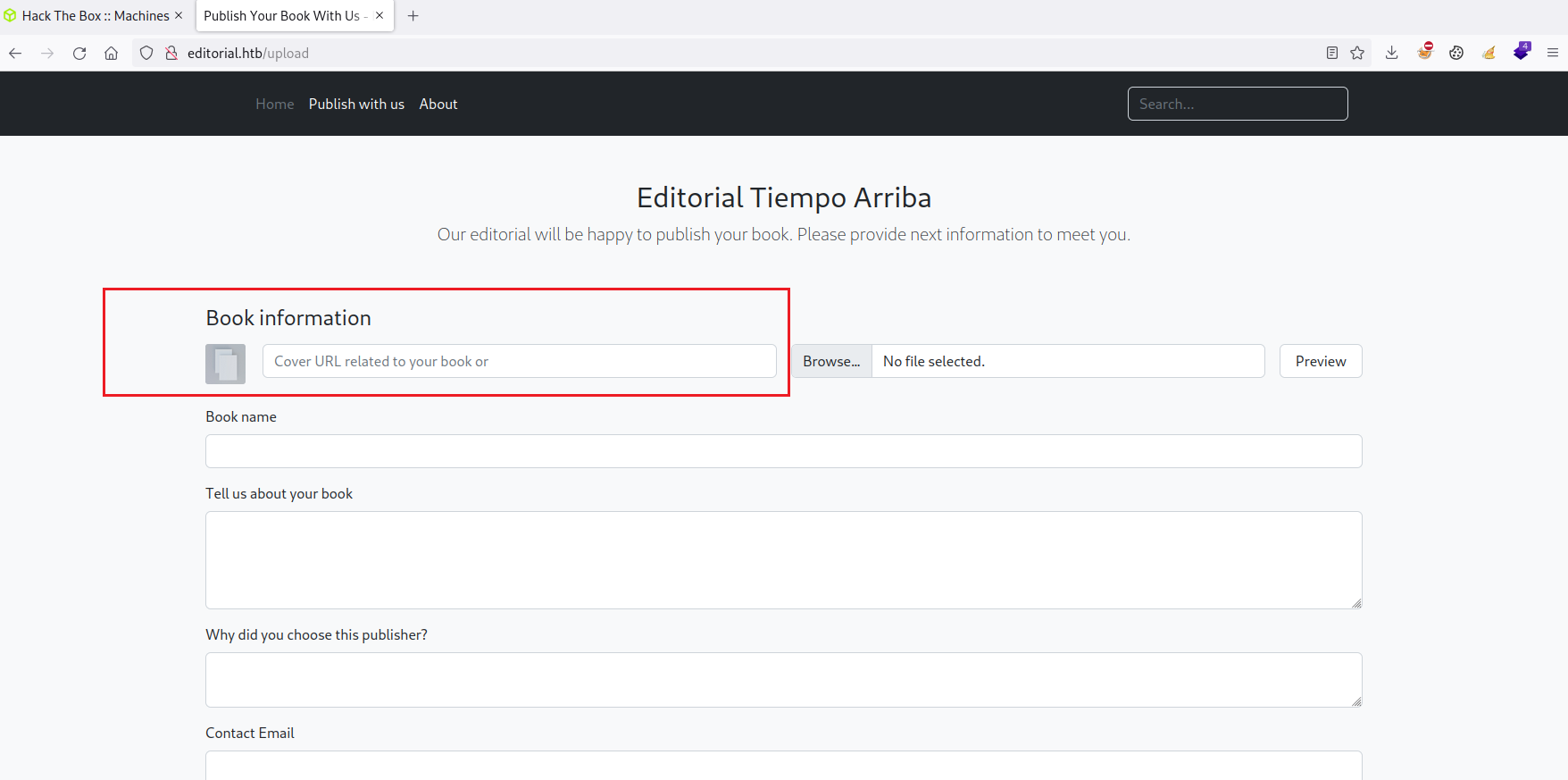
To confirm the vulnerability, just start a local HTTP server on your machine and add your IP in the URL box, then click on "Preview".
An HTTP request is received on the local server, so the SSRF vulnerability is confirmed.

USER
Once we have found the SSRF vulnerability, we have to think of ways of exploiting it. For example, we can try to query the local host looking for open ports, as is explained here:https://adipsharif.medium.com/unveiling-the-techniques-of-finding-server-side-request-forgery-ssrf-in-web-applications-with-a-2ac1dd20ef87
Just send a request to http://127.0.0.1 and capture it with Burpsuite, save the request and add the FUZZ tag to the ports field. The resulting file should be something similar to this:
Now fuzz with ffuf for open ports, use a wordlist of common HTTP ports such as this: https://github.com/danielmiessler/SecLists/blob/master/Discovery/Infrastructure/common-http-ports.txt
Notice there is a response with different size (Size: 51). If you use the SSRF to send a request to http://127.0.0.1:5000 and inspect the response, you'll find a link to an upload path.

And inspecting the traffic with Burpsuite, we see another response just after this one that contains information about several endpoints. In particular, we will check this one /api/latest/metadata/messages/authors

Let's query this endpoint using again the SSRF.

Credentials are disclosed in the response.

Let's use them to open an SSH session on the host.

Which can be used to retrieve the user flag.
ROOT
Start from the SSH session as user dev and take the opportunity to enumerate the user and the system.
Enumerate the file system, navigate to the ~/apps directory, there is a git repository there. Follow this guide to enumerate the git repository: https://medium.com/stolabs/git-exposed-how-to-identify-and-exploit-62df3c165c37
You can check git status with:
Then check the logs and enumerate the commits with:
Credentials for user prod are disclosed enumerating the commit b73481bb823d2dfb49c44f4c1e6a7e11912ed8ae
Move laterally to user prod

If we enumerate sudo capabilities for user prod, we see there is a Python script we can run as root.
Let's inspect the source code of this Python script.
Notice it is making use of the Python git library (GitPython). Let's check which version of GitPython is installed.
And looking for vulnerabilities affecting this version we find this one: https://www.cvedetails.com/cve/CVE-2022-24439/, and this PoC: https://security.snyk.io/vuln/SNYK-PYTHON-GITPYTHON-3113858
Let's create a malicious exploit in bash scripting
And grant it execution permission.
Now run the exploit taking advantage of the sudo configuration.
Although some errors are reported, the exploit has been successfully executed, so the only thing left is just open a root shell.

You are root.
Last updated